Written by
Yuri ZhangSummary: This post accounts for the BitLocker Recovery Key Active Directory and how to access it. You can find more expertise from m3datarecovery. iBoysoft Data Recovery recover files data including key.
BitLocker Recovery Key Active Directory (AD) is a feature in Windows that allows organizations to store and manage BitLocker recovery keys within an Active Directory environment.
BitLocker recovery key is crucial because it allows users to regain access to their encrypted data in case they forget their password or if there's an issue with the TPM (Trusted Platform Module) hardware.
Key Features and uses of BitLocker Recovery Key Active Directory
When a device is encrypted with BitLocker, the recovery key can be automatically backed up to Active Directory. This ensures that IT administrators can retrieve the recovery key if needed. IT administrators can access the recovery keys for all devices within the organization from a central location. This is useful for managing large numbers of devices.
Only authorized personnel can retrieve the recovery keys from Active Directory, it enhances security by restricting access to sensitive information. And Active Directory can keep an audit trail of who accessed the recovery keys, adding an additional layer of security and accountability. If a user forgets their password or if the TPM fails, the IT department can use the recovery key stored in Active Directory to regain access to the encrypted data.
Note: Organizations can use Group Policy settings to ensure that all BitLocker-enabled devices automatically store their recovery keys in Active Directory. This eliminates the need for manual processes and reduces the risk of recovery keys being lost.
How BitLocker Recovery Key Active Directory works
When BitLocker is enabled on a device, it generates a recovery key. The system checks for Group Policy settings to determine if the recovery key should be stored in Active Directory.
If configured, the recovery key is automatically stored in an attribute of the computer object within Active Directory.
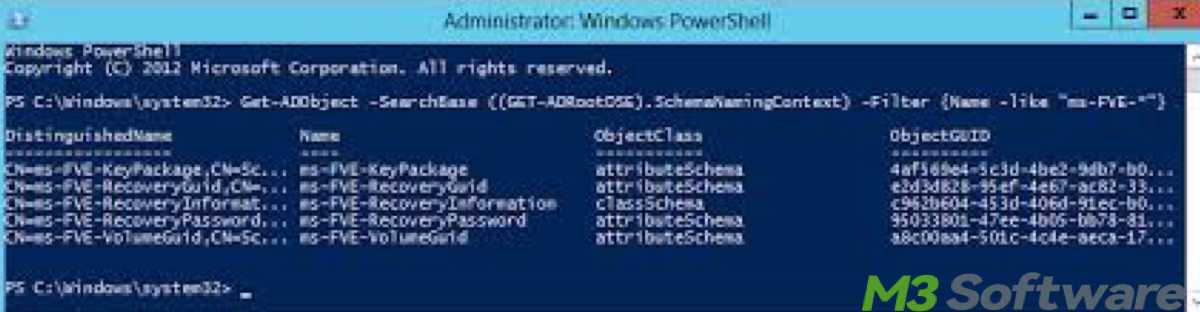
The attribute typically used is ms-FVE-RecoveryInformation.
In case of a need to recover encrypted data, an IT administrator can search for the recovery key in Active Directory using tools such as the Active Directory Users and Computers (ADUC) console or PowerShell scripts.
Share this knowledge to know more about the Windows functions of BitLocker.
How to access BitLocker Recovery Key with Active Directory Users and Computers (ADUC) Console
- Open the Active Directory Users and Computers tool on a domain-joined computer or domain controller.
- In the ADUC console, go to the View menu and select Advanced Features. This will enable you to see additional tabs and attributes.
- Navigate through your Active Directory structure to find the computer object for the machine whose BitLocker recovery key you need. You can use the search function to find the computer object by name.
- Right-click on the computer object and select Properties.
- In the properties window, go to the Attribute Editor tab.
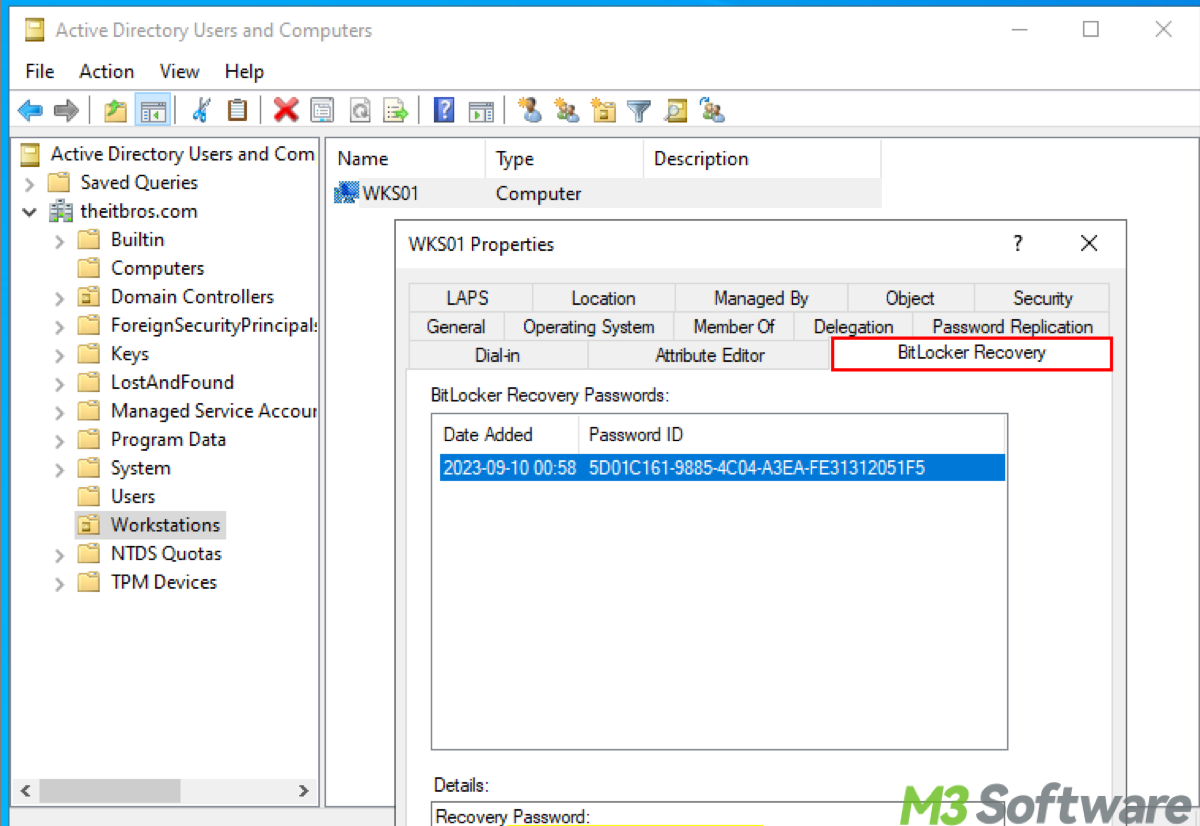
- Look for attributes starting with ms-FVE-. Specifically, you are looking for ms-FVE-RecoveryInformation.
- Click on ms-FVE-RecoveryInformation. You will see entries for BitLocker recovery keys. The ms-FVE-RecoveryPassword attribute within this contains the actual recovery key.
Using PowerShell to access BitLocker Recovery Key in the Active Directory
- Open PowerShell from the search bar.
- Run the following command to retrieve all BitLocker recovery keys in Active Directory:Get-ADObject -Filter { objectClass -eq 'msFVE-RecoveryInformation' } -Property * | Format-List *
- To filter by a specific computer, you can use the command as follows and replace <ComputerName> with the actual name of the computer.Get-ADObject -Filter { objectClass -eq 'msFVE-RecoveryInformation' -and Name -eq '<ComputerName>' } -Property * | Format-List *
- Look for the ms-FVE-RecoveryPassword attribute in the output. This contains the BitLocker recovery key.
Final thoughts
Some may ask if I can search for BitLocker Recovery Key Active Directory directly through File Explorer, but the answer is no. You cannot search for BitLocker recovery keys directly through File Explorer.
File Explorer is a graphical interface primarily designed for navigating and managing files and folders on your local system and network shares. It does not have built-in capabilities to query Active Directory or search for specific attributes like BitLocker recovery keys.
To search for BitLocker recovery keys stored in Active Directory, you typically use administrative tools like the Active Directory Users and Computers (ADUC) console or PowerShell.
For your further reference, also read What is Windows BitLocker.
Comment down below and spread this wisdom to others.
