Written by
Yuri ZhangSummary: This article covers the main questions around BitLocker integration with Active Directory, troubleshooting when recovery information is not visible in Active Directory. iBoysoft DiskGeeker helps if you need a more carefree BitLocker alternative.
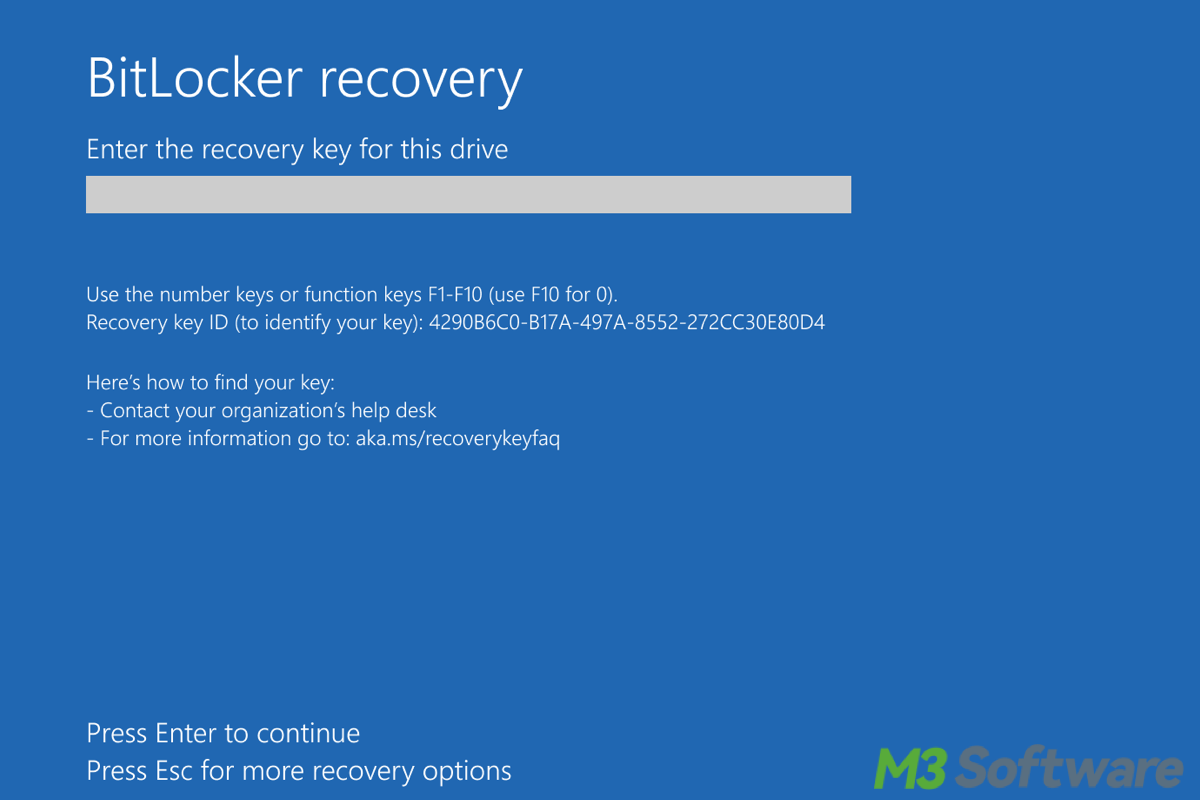
When we see the BitLocker tab missing in Active Directory (AD), we need to keep tabs on the BitLocker. BitLocker is a disk encryption feature built into Windows to protect data on system drives.
AD can be used to manage BitLocker recovery keys, which are vital if we forget passwords or face boot issues. If you feel troublesome, let's delve into multiple ways to address the BitLocker tab missing in AD immediately.
Why is the BitLocker Recovery tab missing in AD
A common issue is the absence of the BitLocker Recovery tab in Active Directory. This often arises due to configuration issues, missing schema extensions, or failure to back up recovery information to AD.
- If the recovery key was not backed up to AD, the recovery tab will not appear. Ensure that BitLocker was enabled and the recovery information was properly backed up.
- The AD schema must be extended to support BitLocker recovery attributes. Without this, Active Directory will not be able to store or display BitLocker recovery information.
- The correct Group Policy setting must be enabled to store BitLocker recovery information in AD. If this policy is not set, recovery information will not be stored, and the tab won't appear.
Troubleshooting BitLocker Recovery tab missing in AD
After knowing BitLocker integration with Active Directory, we can solve it in terms of the above reasons.
1. Configure Group Policy Settings to store BitLocker information in AD
A group policy setting might be preventing the BitLocker tab from appearing in Active Directory. Make sure that the "Store BitLocker recovery information in Active Directory Domain Services" policy is enabled.
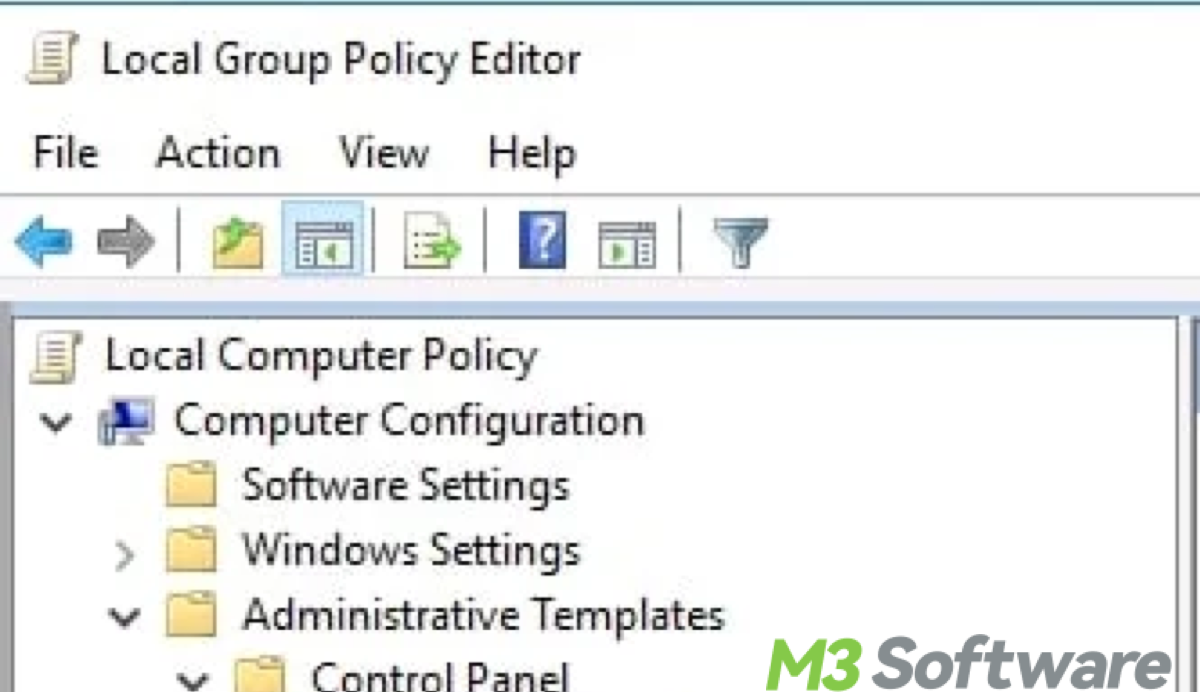
- Press Win + R to open the "Run" dialog, and type gpedit.msc and press Enter to open the Local Group Policy Editor.
- Navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption.
- Find the policy: Store BitLocker recovery information in Active Directory Domain Services (Windows Server 2008 and later).
- Double-click on the policy to open its properties window and select Enabled to enable the policy.
- (Optional) Under Options, you can configure: 'Store recovery information for operating system drives' / 'Store recovery information for fixed data drives' / 'Store recovery information for removable data drives'.
- Click OK to apply the changes.
2. Verify Active Directory schema
The AD schema might not be extended to support BitLocker recovery information. This step is required for BitLocker recovery information to be stored and viewed in Active Directory.
- Download the BitLocker ADMX templates from Microsoft.
- Open PowerShell as Administrator in Start Menu.
- Run the following command to register the necessary BitLocker schema extension libraries for Active Directory.regsvr32 C:\Windows\System32\BitLockerDriveEncryption.dll
3. Back up BitLocker recovery information
If the BitLocker recovery information has not been backed up to AD, the tab will not appear. Ensure that the BitLocker recovery keys are being backed up to Active Directory during the encryption process. Here's how:
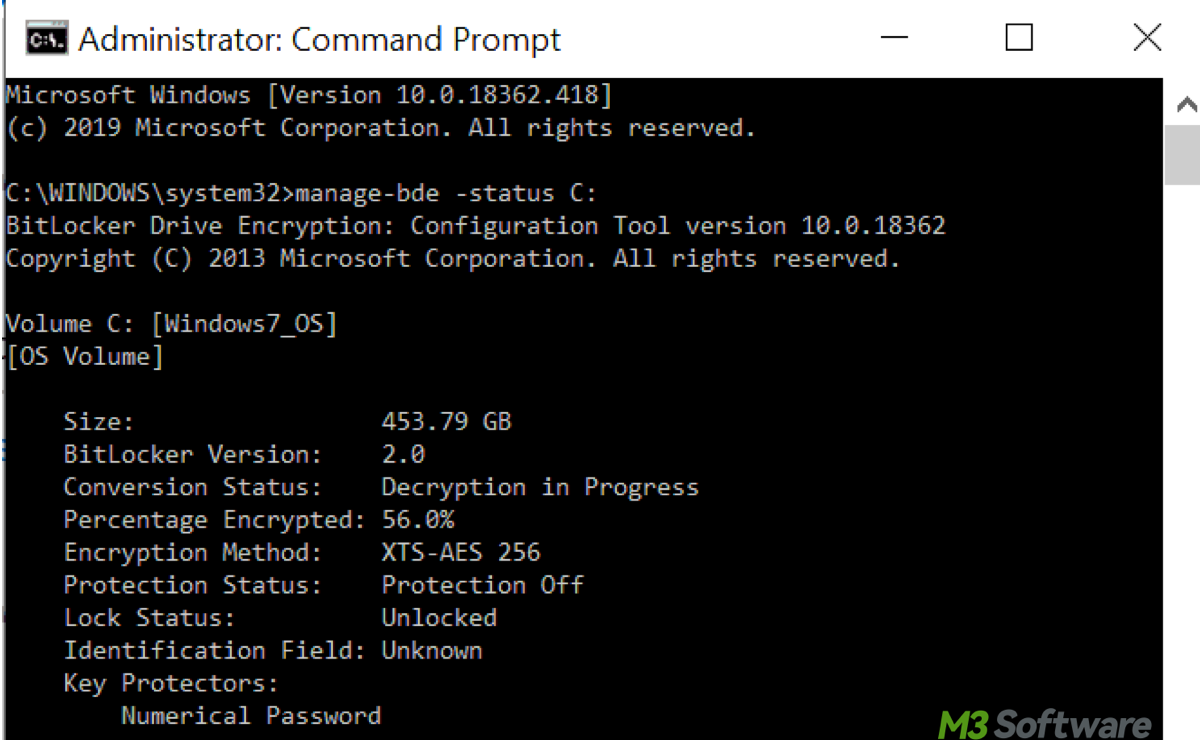
- Open Command Prompt as administrator by searching in the Start Menu.
- Type manage-bde -status and press Enter to check the encryption status.
- If BitLocker is enabled, but the recovery key isn't in Active Directory, you can force it to back up by running the following command:manage-bde -protectors -adbackup C:
Share this post if any of these steps help!
Checking BitLocker encryption status in Active Directory
Before or after troubleshooting the missing issue, you can always check the outcome. BitLocker's encryption status isn't directly visible in Active Directory, but you can check whether BitLocker recovery information has been stored in AD. Here are several methods to check:
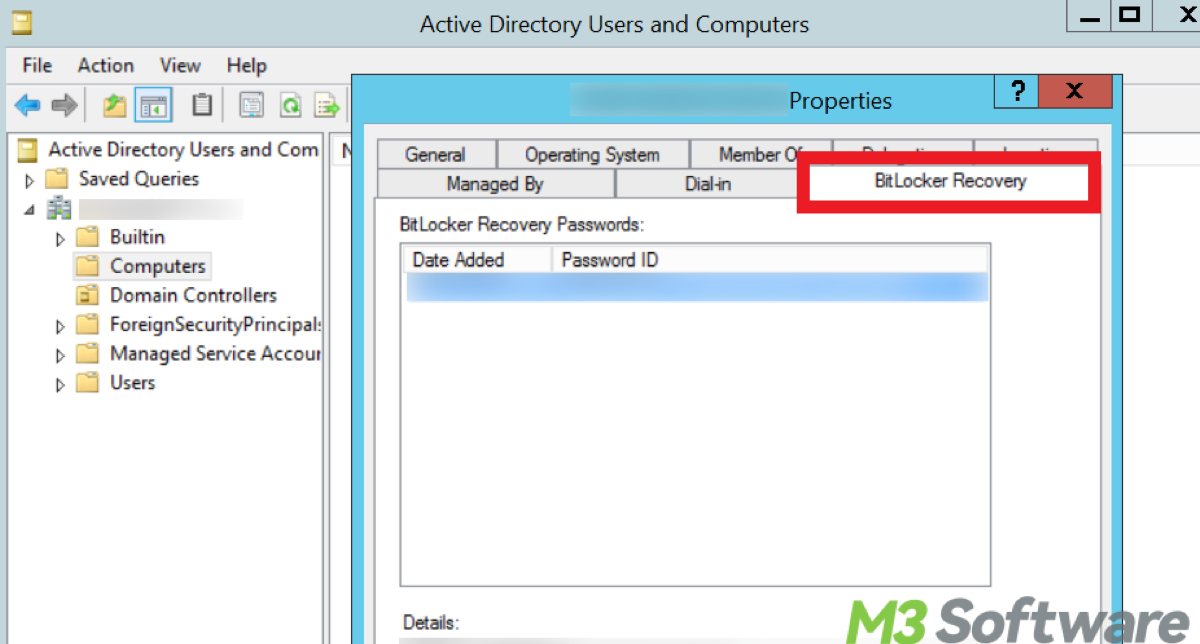
1. Active Directory Users and Computers (ADUC)
Use ADUC to check for the BitLocker Recovery tab in the computer object properties. This tab will show if recovery information is available, indicating that BitLocker is active on the machine. You can open ADUC by pressing Win + R and then typing dsa.msc and pressing Enter.
2. Querying AD attributes
You can query specific Active Directory attributes like msFVE-RecoveryPassword and msFVE-RecoveryGuid using PowerShell to determine if recovery information is stored:Get-ADComputer -Filter {Name -eq "ComputerName"} -Properties msFVE-RecoveryPassword, msFVE-RecoveryGuid If these two attributes are missing, you will need to extend the schema.
3. Checking the BitLocker status on local machines
Use the manage-bde -status command in Command Prompt to check the encryption status locally on a computer. This provides detailed information, including encryption method, protection status, and whether the recovery key is backed up to AD.
4. Automating BitLocker status checks across multiple devices
If you have multiple machines to manage, it becomes cumbersome to check the status manually. Automating the process with PowerShell scripts can make this process more efficient. You can use the following PowerShell script to remotely check the BitLocker status on multiple machines:$computers = @("Computer1", "Computer2", "Computer3") # Replace with actual computer names
foreach ($computer in $computers) {
$status = Invoke-Command -ComputerName $computer -ScriptBlock { manage-bde -status }
Write-Output "BitLocker Status for $computer:"
Write-Output $status
}
Final thought
Integrating BitLocker with Active Directory allows administrators to ensure that recovery information is securely stored and accessible in case of an emergency. Configuring and troubleshooting BitLocker with AD requires careful attention to Group Policy settings, schema extensions, and backup procedures for recovery keys.
Whether you have heard of or haven't heard of, used or not used BitLocker, it is worth knowing this robust encryption feature. Anyhow, there are some issues you may not get resolved, but iBoysoft DiskGeeker for Windows will not keep you out on a limb as a BitLocker alternative with more basic operation and more various functions.
Related articles
Recognize the Power of BitLocker Folder and Drive Protection
Is BitLocker Encryption Really Broken? Debunking the Myths
An Accomplishing Win Guide to Fix Stuck BitLocker Encryption
Spread this post to help more be free from the affliction of BitLocker missing problem.
